Earlier today, a friend of mine notified me of something strange going on with his Facebook account; a message containing only an image (an .svg file in reality) had been sent automatically, effectively bypassing Facebook's file extension filter:
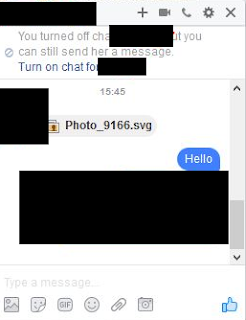 |
| 'Photo_9166.svg' |
What is an .svg file? From Wikipedia:
Scalable Vector Graphics (SVG) is an XML-based vector image format for two-dimensional graphics with support for interactivity and animation. The SVG specification is an open standard developed by the World Wide Web Consortium (W3C) since 1999.This means, more specifically, that you can embed any content you want (such as JavaScript). Moreover, any modern browser will therefore be able to open this file.
Contents of our 'photo' are as follows:
| Copy of file on Pastebin here |
It's a heavily obfuscated script, which, after opening, redirects you to the following website:
| Fake Youtube - "You must install the codec extension to watch this video." |
A website purporting to be Youtube, including a video from Facebook - of course, you'll need to install an additional extension to view it :)
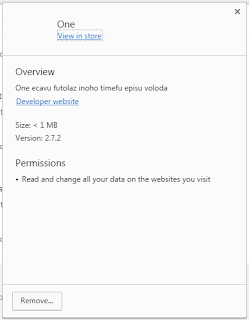
The extension has no icon and thus seems invisible and has the following permissions:
Currently, I'm not exactly sure what this extension is supposed to do beside spreading itself automatically via Facebook (harvesting your credentials in the process), but likely it downloads other malware to your machine.
One of my security colleagues had in fact noticed similar behavior and got ransomware (Locky) as payload:
Confirmed! #Locky spreading on #Facebook through #Nemucod camouflaged as .svg file. Bypasses FB file whitelist. https://t.co/WYRE6BlXIF pic.twitter.com/jgKs29zcaG— peterkruse (@peterkruse) November 20, 2016
The extensions' description can be one of the following, and seem semi-random. Note that other variations are possible:
One ecavu futolaz corabination timefu episu voloda
Ubo oziha jisuyes oyemedu kira nego mosetiv zuhum
The Facebook security team as well as Google Chrome's store security team have been notified.
UPDATE 22/11/2016:
- The rogue Chrome extensions are removed from the store.
- Facebook is now filtering for SVG files as well:
| Test.svg, containing just a window.alert() method |
Removal
Remove the malicious extension from your browser immediately:
Additionally, run a scan with your antivirus and change your Facebook password afterwards.
Notify your friends you sent a malicious file, or in the other case, let your friend know he/she is infected. If you keep receiving the same message from your friend, you may want to temporarily block their messages.
Conclusion
As always, be wary when someone sends you just an 'image' - especially when it is not how he or she would usually behave.
Additionally, even though both Facebook and Google have excellent security controls/measures in place, something bad can always happen.
For those interested, all related files have been uploaded to VirusTotal, and their hashes and domains can be found, as always, on AlienVault's OTX: